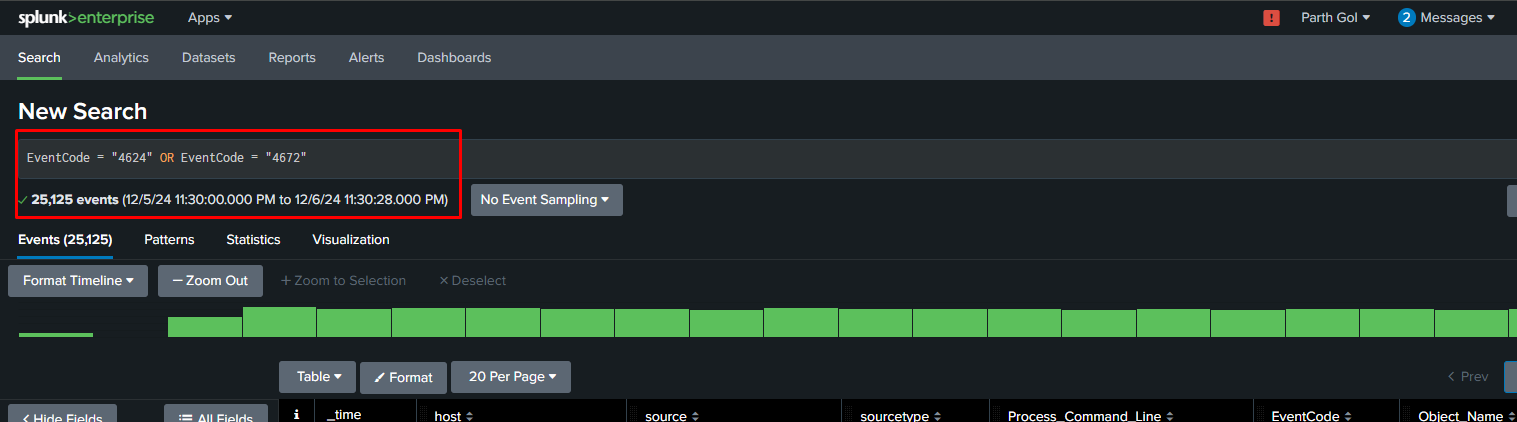
Overview
Pass-the-Hash (PtH) attacks can be detected through careful monitoring of Windows Event logs across both source and target systems. The detection strategy focuses on correlating multiple event IDs that indicate potential credential abuse and lateral movement:
On source systems, several key Windows Event IDs can help detect Pass-the-Hash attacks. Event ID 4688 monitors process creation, particularly focusing on known credential dumping tools. Event ID 4624 with Logon Type 9 indicates when explicit credentials are being used, while Event ID 4648 captures attempts to use explicit credentials for network authentication.
For target systems, the detection strategy involves monitoring Event ID 4776 for NTLM authentication attempts, Event ID 4624 (Logon Type 3) for network logons specifically using the NTLM authentication package, Event ID 4672 which shows when special privileges are assigned to new logons, and Event ID 5140 which tracks network share access activity.
Log Collection Strategy for AD Environment
Windows Event Log Collection
To effectively collect logs from Active Directory environment, configure the following:
- Group Policy Settings:
- Enable Advanced Audit Policy Configuration
- Configure “Security Settings > Advanced Audit Policy Configuration”
- Enable auditing for Account Logon, Account Management, and Directory Service Access
Event Event Log Settings
Configure the following audit policies via Group Policy to detect Pass-the-Hash attacks:
- Process Creation (audit policy, Sysmon)
- Network connection (audit policy, Sysmon)
- Authentication log (audit policy)
To enable these policies:
auditpol /set /subcategory:"Credential Validation" /success:enable /failure:enable
auditpol /set /subcategory:"Security Group Management" /success:enable
auditpol /set /subcategory:"Process Creation" /success:enable
auditpol /set /subcategory:"Logon" /success:enable /failure:enable
Performance Considerations
When implementing log collection, consider:
- Network bandwidth impact of log forwarding
- Storage requirements for historical data
- Processing overhead on Domain Controllers
- Retention policy compliance requirements
PtH via Mimikatz Remote Login
Description
The Pass-the-Hash (PtH) technique involves extracting credential hashes from memory where a domain admin session is active. This process leverages the extracted hash to create a new authenticated session, which provides access to domain controller resources without requiring the actual password.
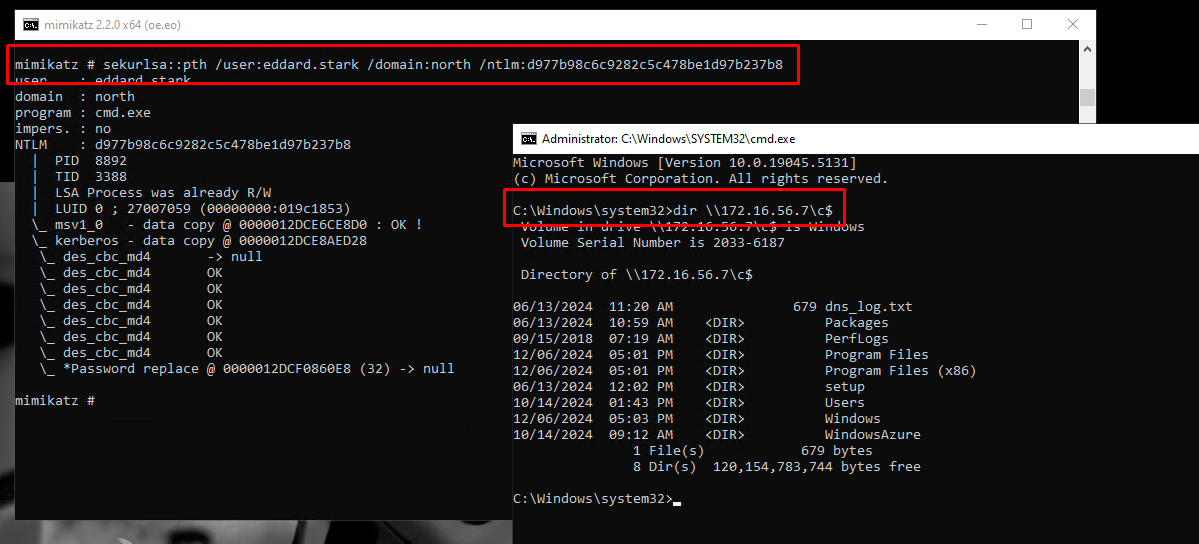
Pass-the-Hash Attack Flow using Mimikatz for DC File Access Remotely
Event Generated During Execution:
Source Host Event (Infected Host)
| # | Event Log | Event ID | Task Category | Event Details |
|---|---|---|---|---|
| 1 | Security | 4688 | Process Creation | A new process has been created. Creator Subject: Security ID: NORTH\parth.gol Account Name: parth.gol Account Domain: NORTH Logon ID: 0x9473E Target Subject: Security ID: NULL SID Account Name: - Account Domain: - Logon ID: 0x0 Process Information: New Process ID: 0x2fd8 New Process Name: C:\Users\parth.gol\Desktop\mimikatz.exe Token Elevation Type: %%1938 Mandatory Label: Mandatory Label\Medium Mandatory Level Creator Process ID: 0x1b5c Creator Process Name: C:\Windows\System32\cmd.exe Process Command Line: mimikatz.exe |
| 2 | Security | 4624 | Successful Logon | An account was successfully logged on. Subject: Security ID: NORTH\parth.gol Account Name: parth.gol Account Domain: NORTH Logon ID: 0x94604 Logon Information: Logon Type: 9 Restricted Admin Mode: - Virtual Account: No Elevated Token: Yes Impersonation Level: Impersonation New Logon: Security ID: NORTH\parth.gol Account Name: parth.gol Account Domain: NORTH Logon ID: 0x701DE77 Linked Logon ID: 0x0 Network Account Name: eddard.stark Network Account Domain: north Logon GUID: {00000000-0000-0000-0000-000000000000} Process Information: Process ID: 0x293c Process Name: C:\Windows\System32\svchost.exe Network Information: Workstation Name: - Source Network Address: ::1 Source Port: 0 Detailed Authentication Information: Logon Process: seclogo Authentication Package: Negotiate Transited Services: - Package Name (NTLM only): - Key Length: 0 |
| 3 | Security | 4672 | Special Logon | Special privileges assigned to new logon. Subject: Security ID: NORTH\parth.gol Account Name: parth.gol Account Domain: NORTH Logon ID: 0x701DE77 Privileges: SeSecurityPrivilege SeTakeOwnershipPrivilege SeLoadDriverPrivilege SeBackupPrivilege SeRestorePrivilege SeDebugPrivilege SeSystemEnvironmentPrivilege SeImpersonatePrivilege SeDelegateSessionUserImpersonatePrivilege |
| 4 | Security | 4648 | Attempted Using Credentials | A logon was attempted using explicit credentials. Subject: Security ID: NORTH\parth.gol Account Name: parth.gol Account Domain: NORTH Logon ID: 0x701DE77 Logon GUID: {00000000-0000-0000-0000-000000000000} Account Whose Credentials Were Used: Account Name: eddard.stark Account Domain: north Logon GUID: {00000000-0000-0000-0000-000000000000} Target Server: Target Server Name: winterfell.north.sevenkingdoms.local Additional Information: winterfell.north.sevenkingdoms.local Process Information: Process ID: 0x4 Process Name: - Network Information: Network Address: 172.16.56.11 Port: 445 |
Domain Controller (Target Host)
| # | Event Logs | Event ID | Task Category | Event Details |
|---|---|---|---|---|
| 1 | Security | 4776 | NTLM Authentication | The computer attempted to validate the credentials for an account. Authentication Package: MICROSOFT_AUTHENTICATION_PACKAGE_V1_0 Logon Account: eddard.stark Source Workstation: 4COREWORKSTATIO Error Code: 0x0 |
| 2 | Security | 4672 | Special Privileges Assigned | Special privileges assigned to new logon. Subject: Security ID: NORTH\eddard.stark Account Name: eddard.stark Account Domain: NORTH Logon ID: 0x2A69E8C Privileges: SeSecurityPrivilege SeBackupPrivilege SeRestorePrivilege SeTakeOwnershipPrivilege SeDebugPrivilege SeSystemEnvironmentPrivilege SeLoadDriverPrivilege SeImpersonatePrivilege SeDelegateSessionUserImpersonatePrivilege SeEnableDelegationPrivilege |
| 3 | Security | 4624 | Successful Logon | An account was successfully logged on. Subject: Security ID: NULL SID Account Name: - Account Domain: - Logon ID: 0x0 Logon Information: Logon Type: 3 Restricted Admin Mode: - Virtual Account: No Elevated Token: Yes Impersonation Level: Impersonation New Logon: Security ID: NORTH\eddard.stark Account Name: eddard.stark Account Domain: NORTH Logon ID: 0x2A69E8C Linked Logon ID: 0x0 Network Account Name: - Network Account Domain: - Logon GUID: {00000000-0000-0000-0000-000000000000} Process Information: Process ID: 0x0 Process Name: - Network Information: Workstation Name: 4COREWORKSTATIO Source Network Address: 172.16.56.4 Source Port: 49367 Detailed Authentication Information: Logon Process: NtLmSsp Authentication Package: NTLM Transited Services: - Package Name (NTLM only): NTLM V2 Key Length: 128 |
| 4 | Security | 4627 | Group Membership Information | Group membership information. Subject: Security ID: NULL SID Account Name: - Account Domain: - Logon ID: 0x0 Logon Type: 3 New Logon: Security ID: NORTH\eddard.stark Account Name: eddard.stark Account Domain: NORTH Logon ID: 0x2D252D4 Event in sequence: 1 of 1 Group Membership: NORTH\Domain Users Everyone BUILTIN\Administrators BUILTIN\Users BUILTIN\Pre-Windows 2000 Compatible Access BUILTIN\Remote Desktop Users NT AUTHORITY\NETWORK NT AUTHORITY\Authenticated Users NT AUTHORITY\This Organization NT AUTHORITY\NTLM Authentication Mandatory Label\High Mandatory Level |
| 5 | Security | 5156 | Permitted Connections | The Windows Filtering Platform has permitted a connection. Application Information: Process ID: 3088 Application Name: \device\harddiskvolume2\windows\system32\dns.exe Network Information: Direction: Inbound Source Address: 172.16.56.4 Source Port: 62035 Destination Address: 172.16.56.7 Destination Port: 53 Protocol: 17 Filter Information: Filter Run-Time ID: 113944 Layer Name: Receive/Accept Layer Run-Time ID: 44 |
| 6 | Security | 5140 | File Share Access | A network share object was accessed. Subject: Security ID: NORTH\eddard.stark Account Name: eddard.stark Account Domain: NORTH Logon ID: 0x2D252D4 Network Information: Object Type: File Source Address: 172.16.56.4 Source Port: 56351 Share Information: Share Name: \*\C$ Share Path: \??\C:<br> Access Request Information: Access Mask: 0x1 Accesses: ReadData (or ListDirectory) |
Missing Events
Several key events may be missing from the initial logging window, such as network access events that enhance visibility, including Event ID 5145 for detailed network share access checks, Event ID 5140 for network share object access activity, and Event ID 5156 for permitted network connections through Windows Filtering Platform. These network events are essential for tracking connection patterns and file access attempts during lateral movement. While these events provide valuable security insights, they can generate significant noise in logging systems.
Confirmed Attack Execution
- Source Host: Event ID 4688 shows the creation of “mimikatz.exe” process, followed by Event ID 4624 with logon type 9 and Event ID 4648 showing explicit credential use for “eddard.stark” account.
title: Pass-the-Hash Detection - Explicit Credential Usage (Eddard Stark)
description: Detects potential Pass-the-Hash attacks by monitoring explicit credential usage for specific account
id: 8f924be1-817f-4c11-9c3c-87c4c8a8f8d1
status: experimental
author: Parth Gol
date: 2024/12/06
tags:
- attack.t1550.002
- attack.lateral_movement
- attack.credential_access
logsource:
product: windows
service: security
detection:
selection:
EventID: 4648
AccountName: 'eddard.stark'
Network_Address: '171.16.56.7'
Description: 'A logon was attempted using explicit credentials'
condition: selection
fields:
- ComputerName
- SubjectUserName
- AccountName
- AccountDomain
- Network_Address
- TargetServerName
falsepositives:
- Legitimate administrative activities
- Authorized account usage
level: high
To enhance detection, we can incorporate lists of domain users and IPs directly in the Sigma rule. While these lists can also be maintained in external files, here’s an example with inline lists:
lists:
domain_users:
type: string
items:
- 'eddard.stark'
- 'robb.stark'
- 'arya.stark'
- 'sansa.stark'
- 'brandon.stark'
domain_controllers:
type: string
items:
- '172.16.56.11'
- '172.16.56.12'
- '172.16.56.13'
detection:
selection:
EventID: 4648
AccountName|contains: $domain_users
Network_Address|contains: $domain_controllers
Description: 'A logon was attempted using explicit credentials'
condition: selection
This approach allows for easy maintenance of the monitored accounts and IP addresses directly within the rule definition. You can also use an external file to maintain this list, which can be dynamically updated when you create new resources in your environment.
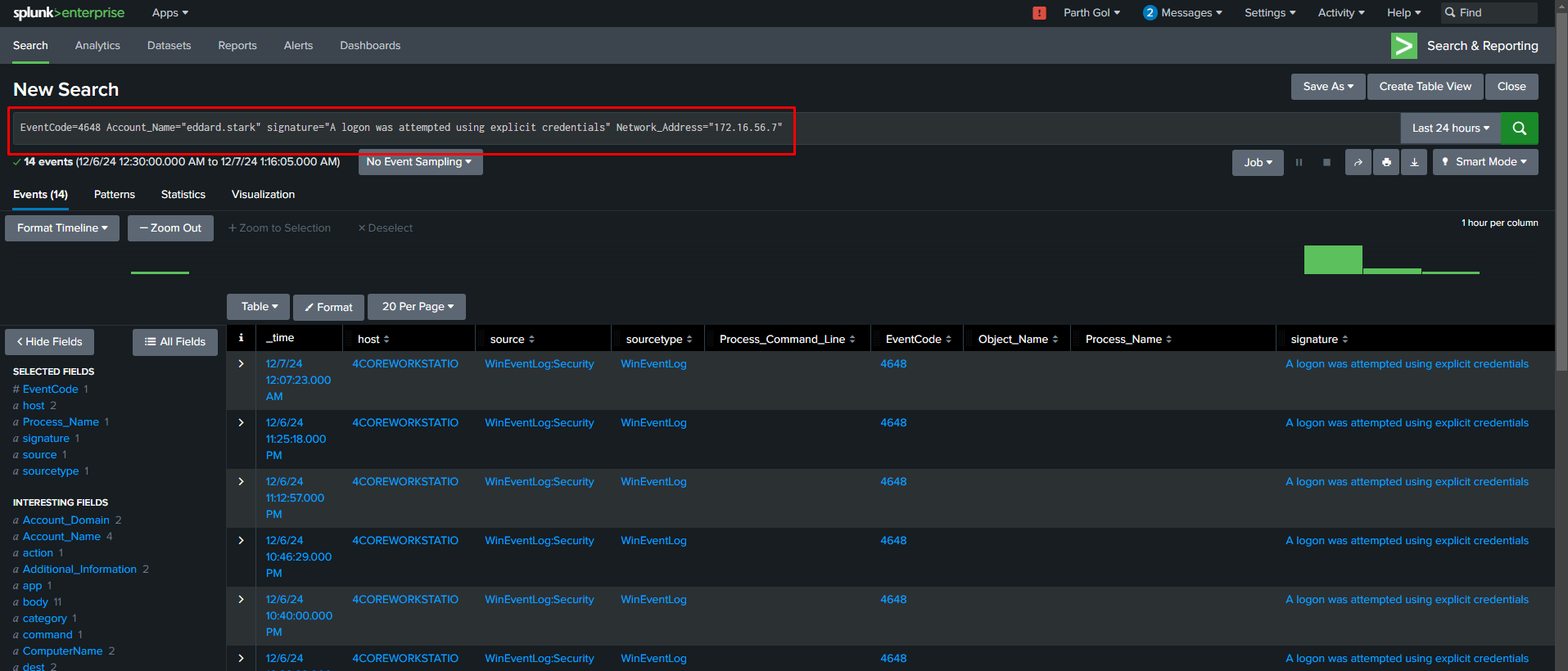
Event log search in Splunk using Sigma rule SPL converted query
- Target Host (Domain Controller): Event ID 4776 confirms NTLM authentication attempt, followed by Event ID 4624 (logon type 3) and Event ID 4672 showing privileged access being granted to the account “eddard.stark”.
title: Detect Pass-the-Hash via Remote Logon
description: Detects potential Pass-the-Hash attacks by monitoring specific Windows Security events where NTLM authentication is used for remote logins.
id: 95aed5a8-b716-49c1-96be-40f7b39d2276
status: experimental
author: Parth Gol
date: 2024/12/06
tags:
- attack.t1550.002
- attack.lateral_movement
references:
- https://attack.mitre.org/techniques/T1550/002/
logsource:
category: authentication
product: windows
detection:
selection:
EventID: 4624
LogonType: 3
AuthenticationPackageName: NTLM
# filter_system_accounts:
# TargetUserName|startswith:
# - 'ANONYMOUS LOGON'
# - 'Guest'
# timeframe: 5m
condition: selection
falsepositives:
- Legitimate administrative activities
- System maintenance tasks
- Usage of legacy systems or software requiring NTLM
level: high
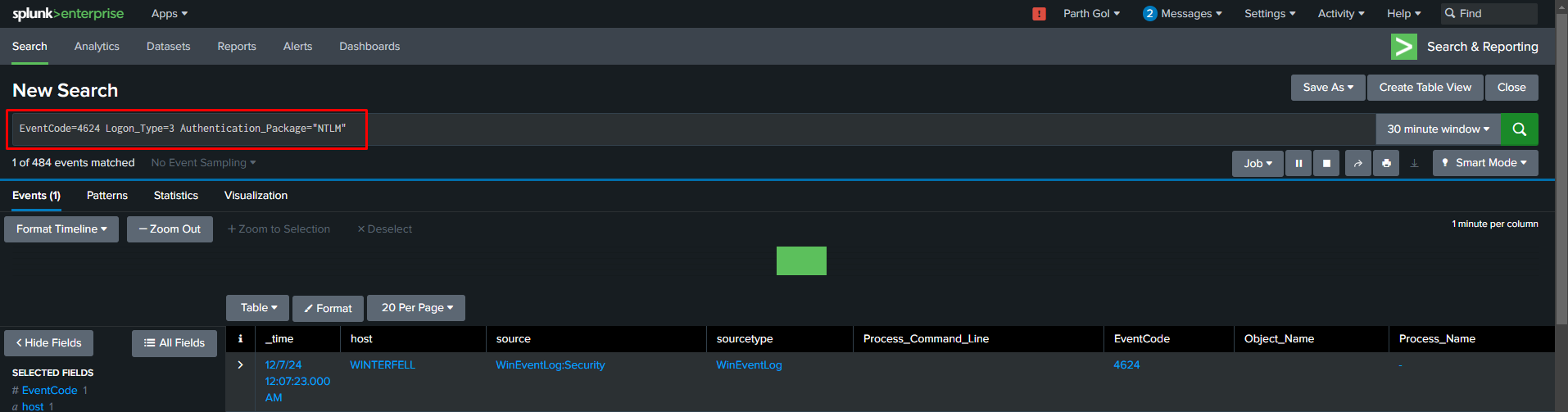
Event log search in Splunk using Sigma rule SPL converted query
Optimizing rules and events
When examining these events in security solutions, you’ll notice that Event IDs 4672 and 4624 generate numerous entries. While optimizing and removing unnecessary events is a separate topic, having too many event logs can be problematic. When pipeline scheduled rules execute, they must match logs against rule queries. Higher log volumes lead to time and space complexity issues. In simple terms, each rule consumes memory and disk space resources, which affects execution time. You can optimize rules by using indexed fields, narrowing time ranges, simplifying conditions, and limiting fields. However, you must implement these optimizations carefully since they might create blind spots in your environment and cause you to miss essential logs and threats.