Table of Contents
Active Directory Logons and Sessions
A logon is the process through which a user authenticates to a computer system. When a user enters their credentials, such as a username and password, Windows verifies the information. If the credentials are valid, Windows establishes a connection between the user and the system. This process of verification and access control is essential for securing resources and ensuring that only authorized users can access the system.
Each logon also has an associated logon type, which specifies how the user accessed the system. For example, logging in locally (physically at the machine) and connecting remotely (through Remote Desktop Protocol) are different types of logons. The logon type affects what kind of access is granted and how the system will manage the user’s interaction.
After a successful logon, a session is created, representing an active, interactive state of a user on the system. In essence, a session is a “container” that holds information about the user’s activities, permissions, and the resources they are accessing. Each logon generates a new session with a unique session ID that Windows uses to keep track of all active users on the system. This session remains active as long as the user is logged in and is essential for managing access controls and user activity.
During this process, user credentials are temporarily stored in the memory of the LSASS (Local Security Authority Subsystem Service) process. LSASS manages security policies, user authentication, and local security, caching credentials to streamline authentication and resource access. Since LSASS holds sensitive information, such as password hashes and Kerberos tickets, it is a frequent target for credential-stealing attacks, including Pass-the-Hash.
Logon types
Understanding logon types and session information is crucial in Active Directory security because these concepts are fundamental to how credential theft and lateral movement attacks work. When attackers gain initial access, they often enumerate session information to identify potential attack paths and target sensitive accounts like domain admins for privilege escalation.
1. Interactive Logon
This logon type occurs when a user logs directly into the physical machine (console), A user sitting at a workstation logs in by entering their credentials on the login screen.
2. Network Logon
Network Logon happens when a user connects to a remote machine using non-interactive services like file shares (SMB), Remote Procedure Call (RPC), or SQL databases. such as Accessing a shared folder on another computer over the network.
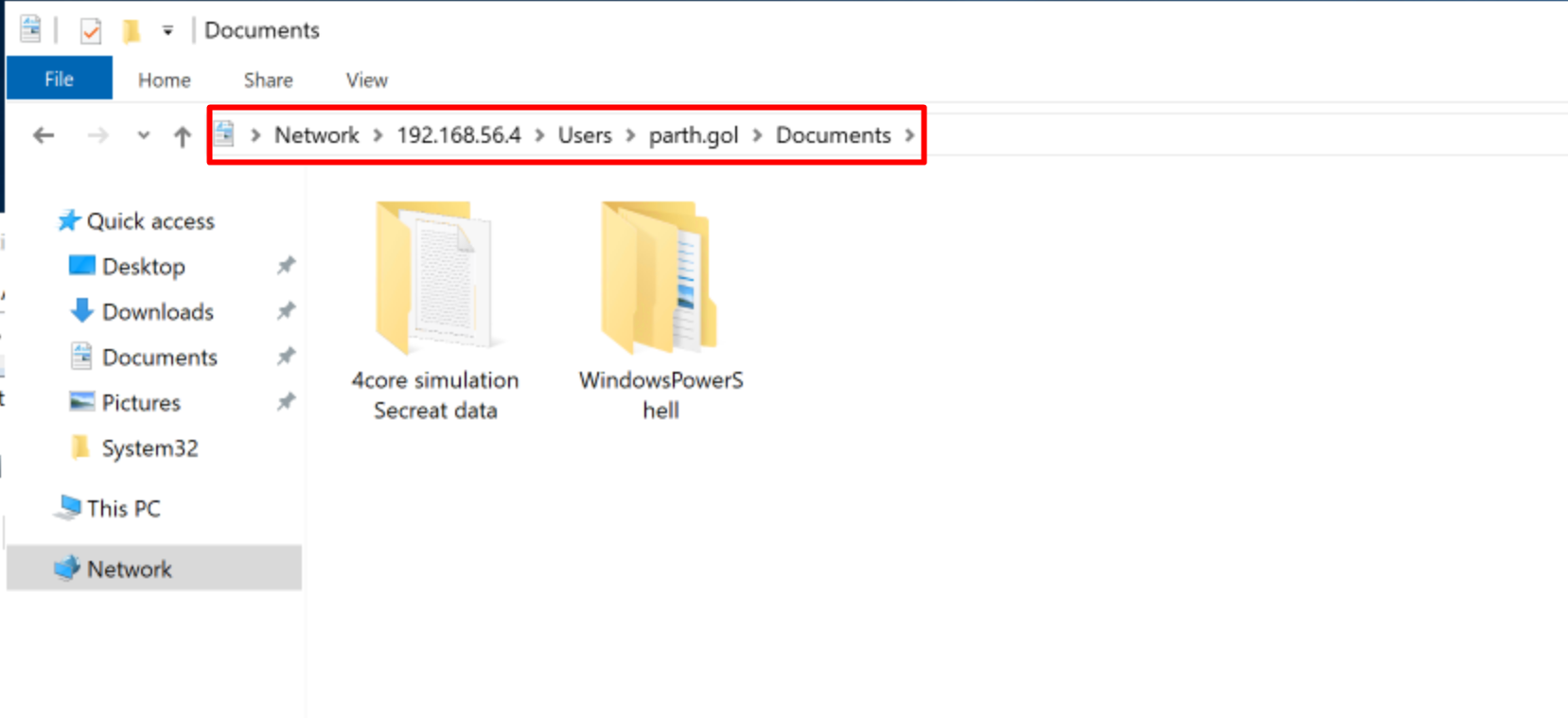
SMB file share access from DC to 4coreworkstation
3. Batch Logon
Batch Logon is specifically designed for scheduled tasks or automated processes running with stored credentials. When a scheduled task is triggered, Windows authenticates the credentials and creates a session similar to an Interactive Logon. This type is often used in automation and system maintenance where user intercession is unnecessary
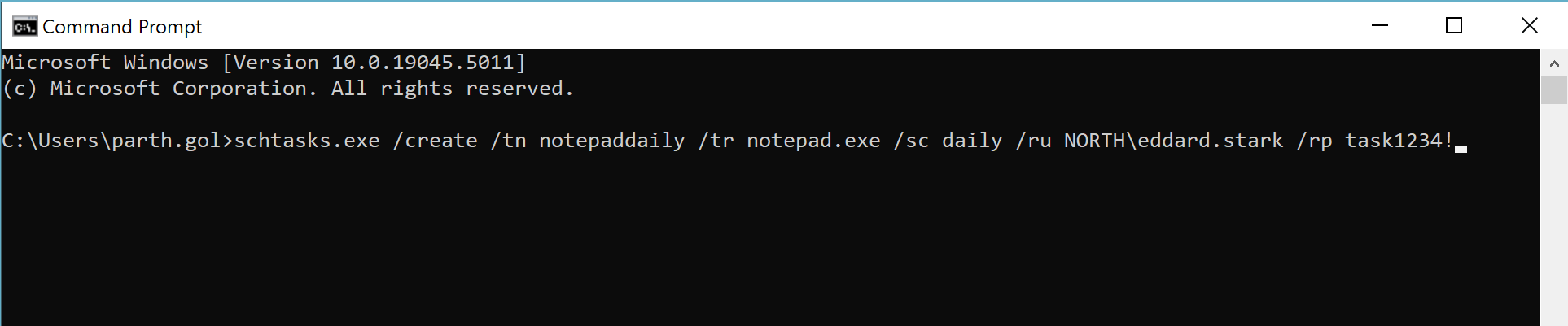
Batch Logon
4. Service Logon
Service Logon is used to start services under a specific user account’s context. Services that need to interact with the system using a specified user’s permissions, such as databases or web servers, often use this logon type. This enables background services to function without direct user intervention, but with specified access rights.
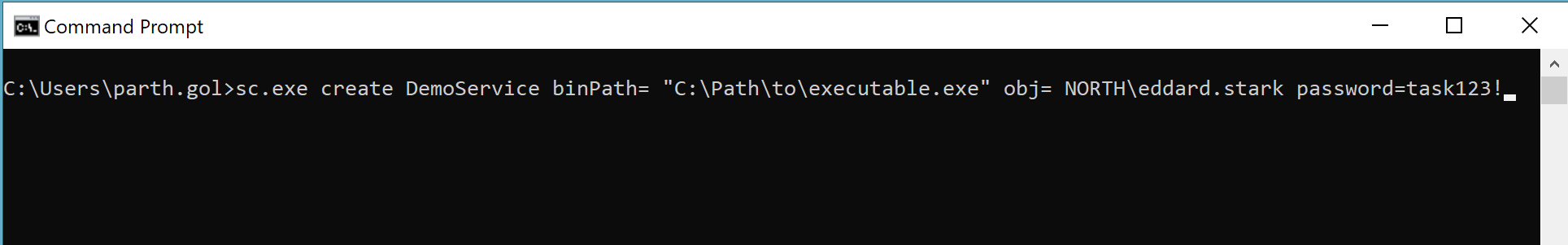
Service Logon
5. Network Cleartext Logon
NetworkCleartext Logon is used in scenarios where credentials need to be passed in plaintext over a secure channel, such as in PowerShell remoting with CredSSP. This logon type allows remote connections to use plaintext credentials securely, primarily for authentication tasks that require explicit credential delegation.
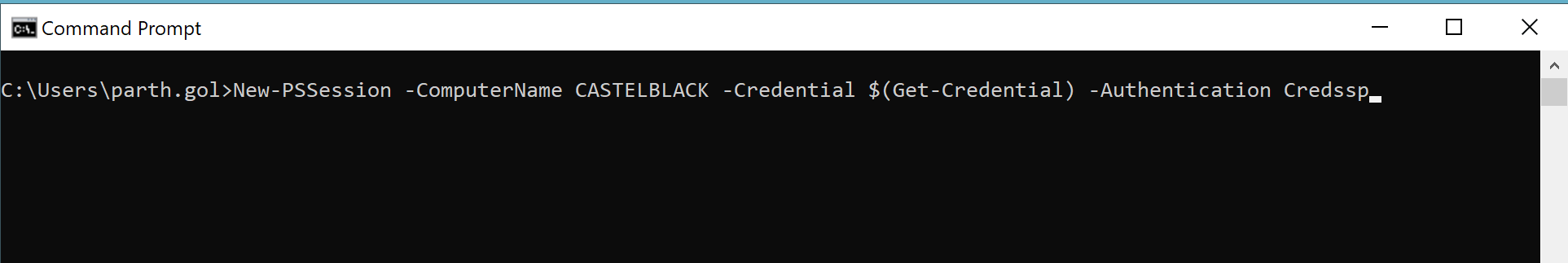
Network Cleartext Logon
6. NewCredentials Logon
NewCredentials Logon allows a user to execute a command or process under a different set of credentials for remote connections only, while keeping their local session. This is often used to access remote resources with elevated permissions without altering the local desktop environment or primary session context.
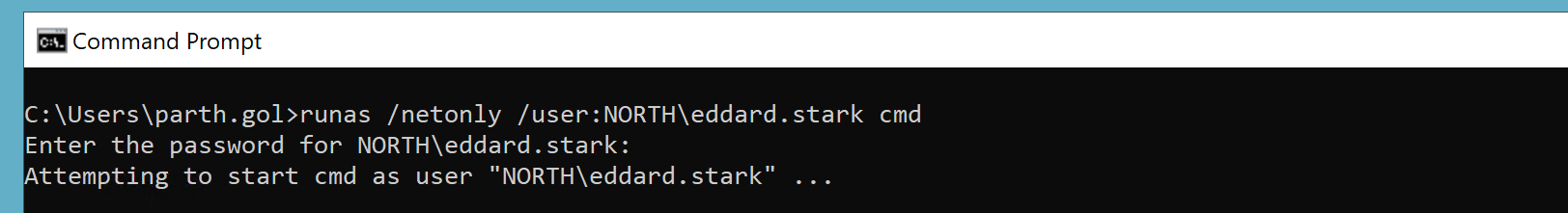
NewCredentials Logon
7. RemoteInteractive Logon
RemoteInteractive Logon is initiated when a user connects to a computer via Remote Desktop Protocol (RDP), allowing full desktop access. RDP uses CredSSP for authentication, ensuring that credentials are securely passed over the network. This logon type is typically used for remote management or support.
remote desktop connection
Session Information Enumeration
Logon session enumeration is a reconnaissance technique used by attackers or red team members to gather information about active sessions on a network and identify possible attack paths within a company’s Active Directory forest.
Tools used for session enumeration include PowerView, a PowerShell-based tool that queries Active Directory for information about logged-on users using Windows APIs such as NetWkstaUserEnum and NetSessionEnum
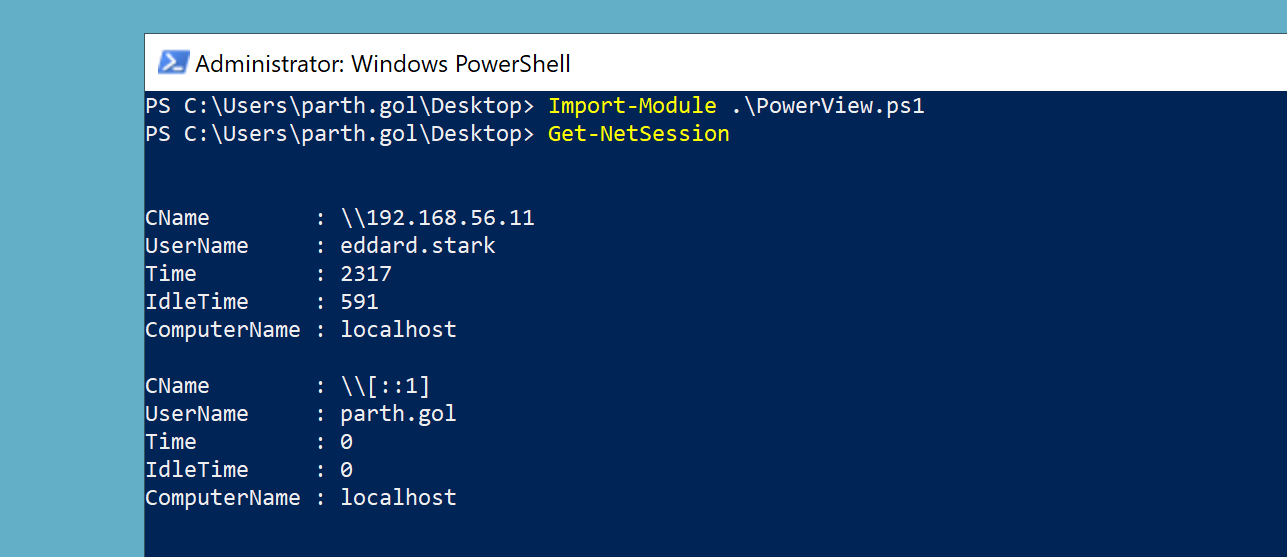
session enumration on local machine
Additionally, we can use custom scripts or tools like query.exe —a built-in Windows tool for querying system information from remote machines. They can make detection difficult by modifying these tools to appear native, blending their Active Directory enumeration activities with normal user behavior.
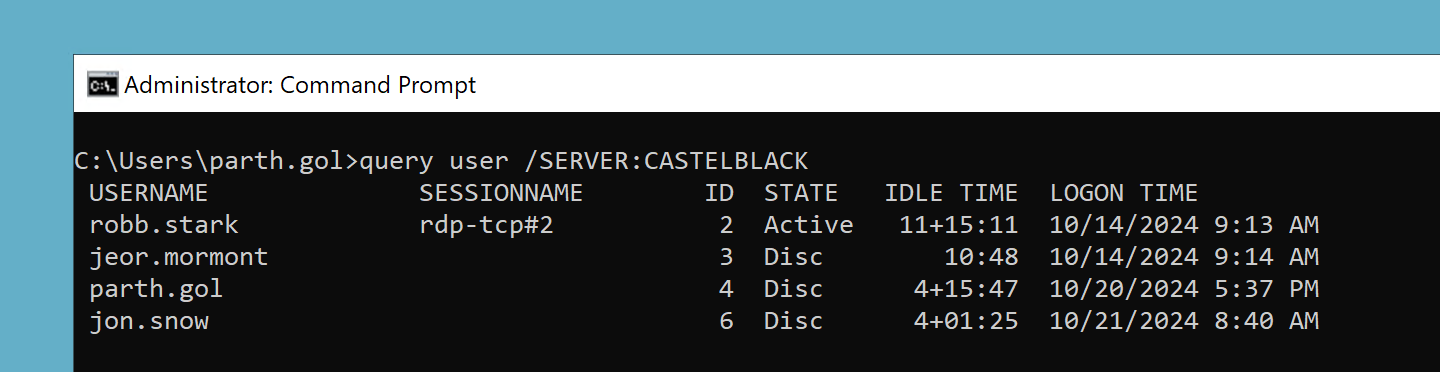
session enumration on remote machine
Privileges Required for Session Information Discovery
In recent versions of Windows, the privileges required to discover session information have evolved, reflecting a significant shift in the security landscape. Previously, authenticated users could leverage tools like NetSessionEnum to enumerate active user sessions. However, this capability has become more restricted in response to growing security concerns. Although the exact timing of this change remains unclear, it is widely believed to have been implemented around Windows 10 version 1607 and Windows Server 2019. The permissions for who can use NetSessionEnum is defined in the registry value SrvsvcSessionInfo in the hive HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\DefaultSecurity.
The new default permissions exclude Authenticated Users, restricting access to only a specific set of roles. Since there are still some methods which can be used to enumerate Logon Session information.