Attempts to Access ntds.dit
| Field | Value |
|---|---|
| Event name | Active Directory Attempts to access ntds.dit |
| Location • Channel | DCSync • Security |
| Operating Systems | Windows 2008 R2, Windows 2012 R2, Windows Server 2016, 2019 and 2022 |
| Category • Subcategory | Object Access • Audit File System |
| Type | audit access object |
| Default setting | configured |
| Event ID | 4663 and 4656 |
Overview
NTDS (Windows NT Directory Services) is the directory services used by Microsoft Windows NT to locate, manage, and organize network resources. The NTDS.dit file is a critical database that stores all Active Directory data, including:
- User accounts and credentials
- Group memberships and permissions
- Security descriptors
- Password hashes
This essential file is stored on domain controllers and serves as the core database for Active Directory functionality. Attempts to access ntds.dit can be detected using the Windows event log. Event IDs 4663 and 4656 of the Audit File System subcategory can be used to audit file system access. Use these events to monitor for both regular and Volume Shadow Copy attempts to read or modify ntds.dit.
Enable Event Auditing
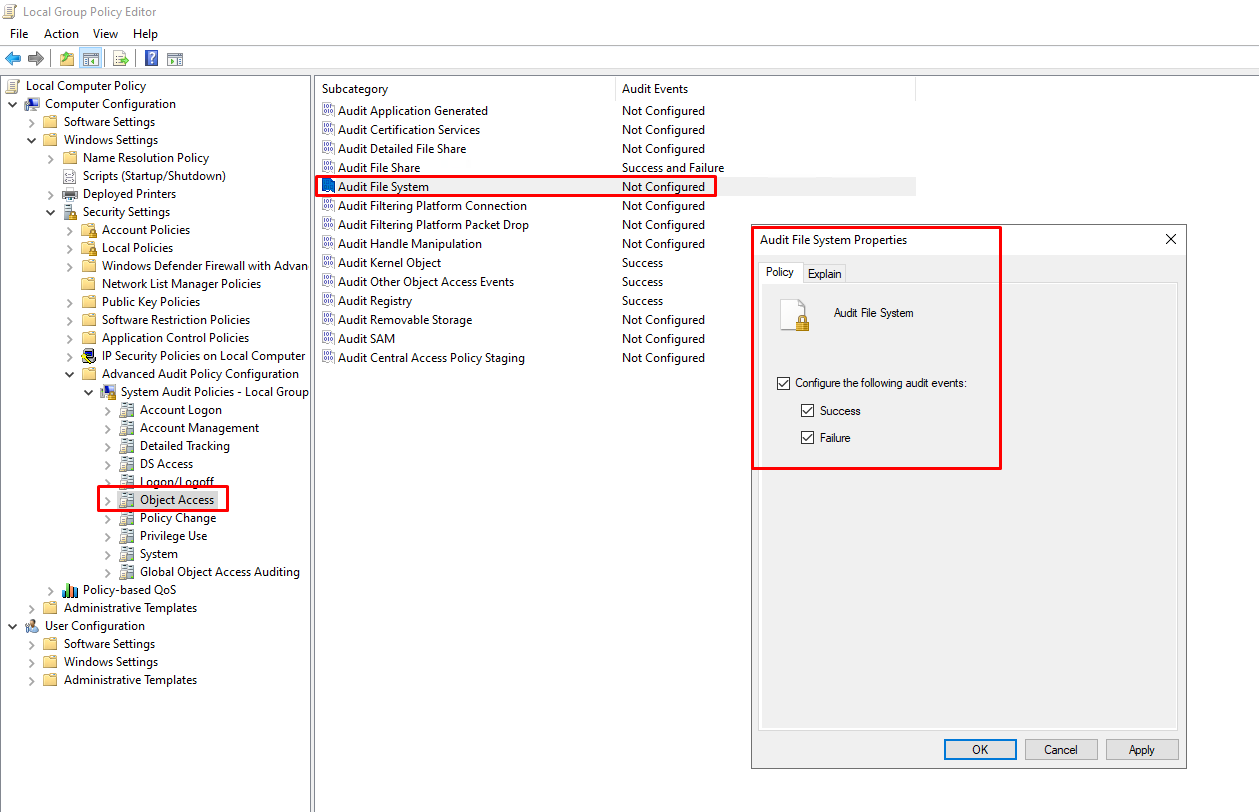
To enable auditing of ntds.dit access attempts, follow these steps in Group Policy:
- Navigate to: Computer Configuration → Windows Settings → Security Settings → Advanced Audit Policy Configuration → System Audit Policies → Object Access
- Double-click “Audit File System”
- Check both “Configure the following audit events” and:
- Success
- Failure
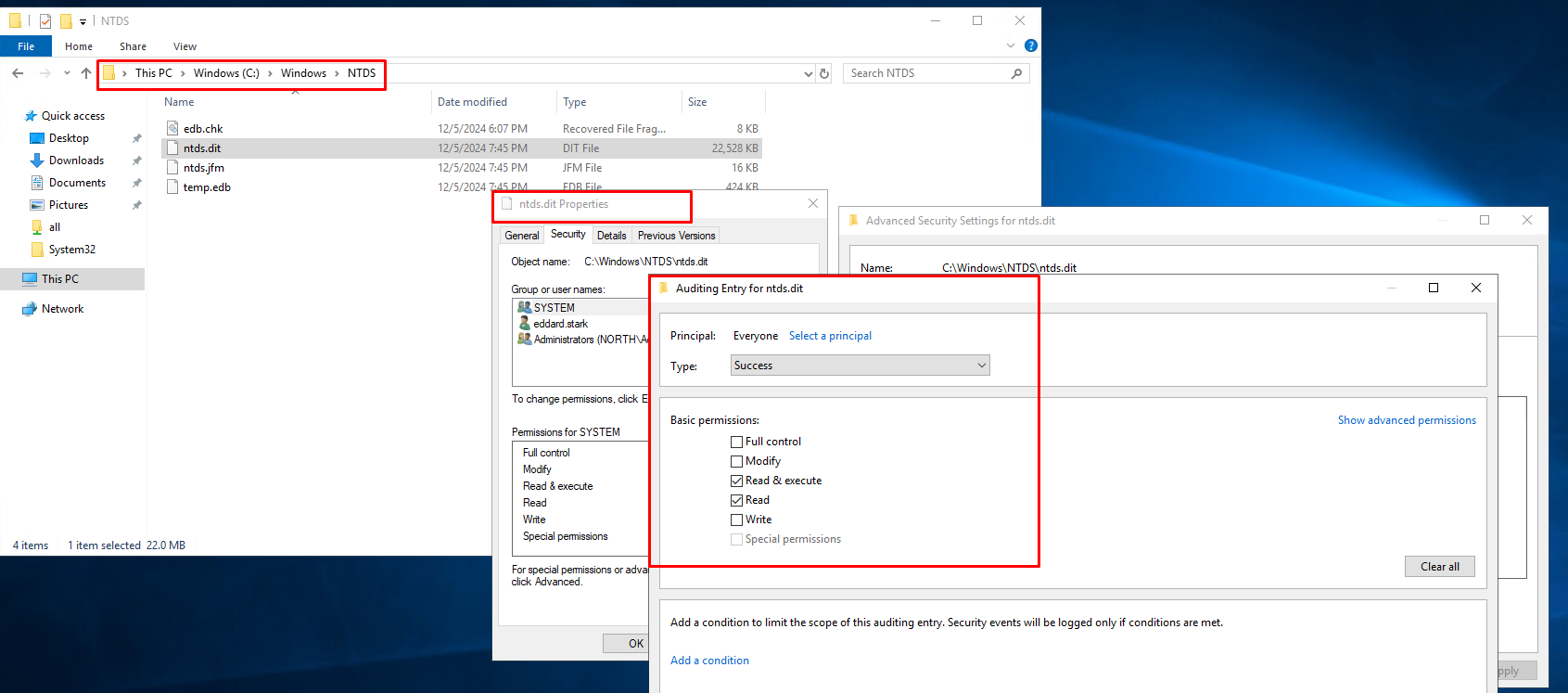
Set up SACL (System Access Control List) on the ntds.dit file located in %SystemRoot%\NTDS\
- Navigate to
%SystemRoot%\NTDS\ - Right-click ntds.dit and select Properties
- Select the Security tab, then click Advanced
- Click the Auditing tab, then Add
- Click
Select a principal - Type
Everyone, click Check Names, then OK - Under Audit Events, select
All - Under Basic Permissions, select these options:
- read
- read and execute
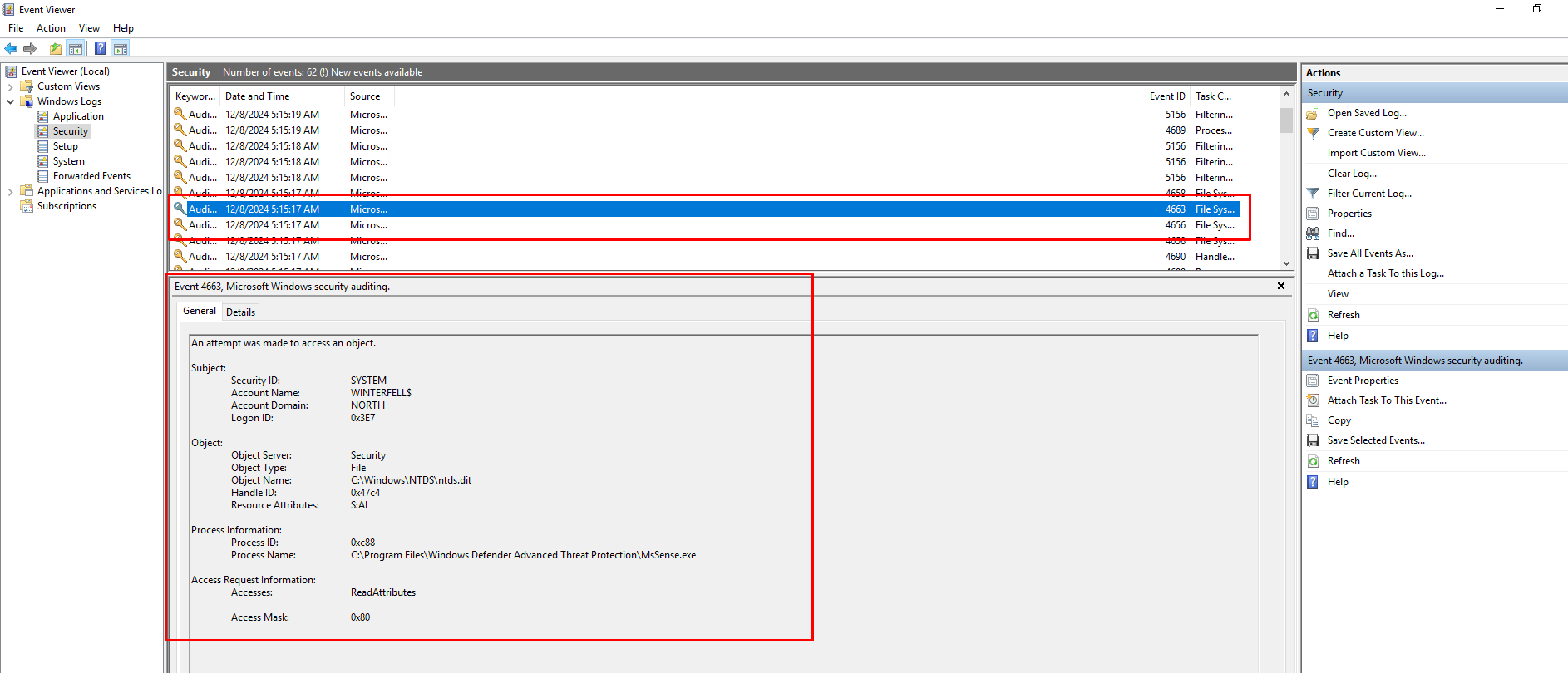
Confirm Attempts to access ntds.dit Event
Check Event Viewer > Windows Logs > Security for Event ID 4663 and 4656 related to ntds.dit access